搜索到
14
篇与
Centos
的结果
-
 自动创建sftp站点账号shell #!/bin/bash #站点目录,用户名根据站点目录生成,多个站点用空格隔开 #例web="test1 test2",生成的用户为sftp_test1 sftp_test2 web="chinaoa sgj" user_dir="/home/public_html/" ssh_dir="/etc/ssh/sshd_config" #配置权限,属主必须为root,权限必须为755,facl也不行 chown root.root ${user_dir} chmod 755 ${user_dir} #设置sebool值 if [[ `getenforce` == "Enforcing" ]];then setsebool ssh_chroot_full_access 1 fi #配置ssh,开启internal-sftp if [[ `grep -w internal-sftp ${ssh_dir} | wc -l` -eq 0 ]];then sed -i "s/Subsystem/#Subsystem/g" ${ssh_dir} echo "Subsystem sftp internal-sftp" >>${ssh_dir} fi for user in ${web};do if [[ `grep -w "Match user sftp_${user}" ${ssh_dir} | wc -l` -eq 0 ]];then #!/bin/bash #站点目录,用户名根据站点目录生成,多个站点用空格隔开 #例web="test1 test2",生成的用户为sftp_test1 sftp_test2 web="chinaoa sgj" user_dir="/home/public_html/" ssh_dir="/etc/ssh/sshd_config" #配置权限,属主必须为root,权限必须为755,facl也不行 chown root.root ${user_dir} chmod 755 ${user_dir} #设置sebool值 if [[ `getenforce` == "Enforcing" ]];then setsebool ssh_chroot_full_access 1 fi #配置ssh,开启internal-sftp if [[ `grep -w internal-sftp ${ssh_dir} | wc -l` -eq 0 ]];then sed -i "s/Subsystem/#Subsystem/g" ${ssh_dir} echo "Subsystem sftp internal-sftp" >>${ssh_dir} fi for user in ${web};do if [[ `grep -w "Match user sftp_${user}" ${ssh_dir} | wc -l` -eq 0 ]];then Match user sftp_${user} ChrootDirectory ${user_dir} X11Forwarding no AllowTcpForwarding no ForceCommand internal-sftp ### END ### EOF fi #添加用户 if [[ `grep -w "sftp_${user}" /etc/passwd | wc -l` -eq 0 ]];then useradd -M -s /bin/false sftp_${user} read -s -t 30 -p "请在30S内输入站点${i}用户密码: " password echo "${password}" |passwd --stdin sftp_${user} echo "用户生成完毕,用户名为: sftp_${user}" else echo "用户sftp_${user}已存在,请检查" fi #赋权对应目录给用户 setfacl -R -d -m u:sftp_${user}:rwx ${user_dir}${user} setfacl -R -m u:sftp_${user}:rwx ${user_dir}${user} #去掉不该有的目录权限,增加安全 cd ${user_dir} setfacl -R -d -m u:sftp_${user}:--- `ls ${user_dir} | grep -v "${user}"` setfacl -R -m u:sftp_${user}:--- `ls ${user_dir} | grep -v "${user}"` done #重启ssh服务 service sshd restart #人性化输出 echo "请使用sftp进行连接,端口号:`netstat -anltp | grep LISTEN | grep sshd | grep "0.0.0.0" | awk '{print $4}' | awk -F: '{print $2}'`"
自动创建sftp站点账号shell #!/bin/bash #站点目录,用户名根据站点目录生成,多个站点用空格隔开 #例web="test1 test2",生成的用户为sftp_test1 sftp_test2 web="chinaoa sgj" user_dir="/home/public_html/" ssh_dir="/etc/ssh/sshd_config" #配置权限,属主必须为root,权限必须为755,facl也不行 chown root.root ${user_dir} chmod 755 ${user_dir} #设置sebool值 if [[ `getenforce` == "Enforcing" ]];then setsebool ssh_chroot_full_access 1 fi #配置ssh,开启internal-sftp if [[ `grep -w internal-sftp ${ssh_dir} | wc -l` -eq 0 ]];then sed -i "s/Subsystem/#Subsystem/g" ${ssh_dir} echo "Subsystem sftp internal-sftp" >>${ssh_dir} fi for user in ${web};do if [[ `grep -w "Match user sftp_${user}" ${ssh_dir} | wc -l` -eq 0 ]];then #!/bin/bash #站点目录,用户名根据站点目录生成,多个站点用空格隔开 #例web="test1 test2",生成的用户为sftp_test1 sftp_test2 web="chinaoa sgj" user_dir="/home/public_html/" ssh_dir="/etc/ssh/sshd_config" #配置权限,属主必须为root,权限必须为755,facl也不行 chown root.root ${user_dir} chmod 755 ${user_dir} #设置sebool值 if [[ `getenforce` == "Enforcing" ]];then setsebool ssh_chroot_full_access 1 fi #配置ssh,开启internal-sftp if [[ `grep -w internal-sftp ${ssh_dir} | wc -l` -eq 0 ]];then sed -i "s/Subsystem/#Subsystem/g" ${ssh_dir} echo "Subsystem sftp internal-sftp" >>${ssh_dir} fi for user in ${web};do if [[ `grep -w "Match user sftp_${user}" ${ssh_dir} | wc -l` -eq 0 ]];then Match user sftp_${user} ChrootDirectory ${user_dir} X11Forwarding no AllowTcpForwarding no ForceCommand internal-sftp ### END ### EOF fi #添加用户 if [[ `grep -w "sftp_${user}" /etc/passwd | wc -l` -eq 0 ]];then useradd -M -s /bin/false sftp_${user} read -s -t 30 -p "请在30S内输入站点${i}用户密码: " password echo "${password}" |passwd --stdin sftp_${user} echo "用户生成完毕,用户名为: sftp_${user}" else echo "用户sftp_${user}已存在,请检查" fi #赋权对应目录给用户 setfacl -R -d -m u:sftp_${user}:rwx ${user_dir}${user} setfacl -R -m u:sftp_${user}:rwx ${user_dir}${user} #去掉不该有的目录权限,增加安全 cd ${user_dir} setfacl -R -d -m u:sftp_${user}:--- `ls ${user_dir} | grep -v "${user}"` setfacl -R -m u:sftp_${user}:--- `ls ${user_dir} | grep -v "${user}"` done #重启ssh服务 service sshd restart #人性化输出 echo "请使用sftp进行连接,端口号:`netstat -anltp | grep LISTEN | grep sshd | grep "0.0.0.0" | awk '{print $4}' | awk -F: '{print $2}'`" -
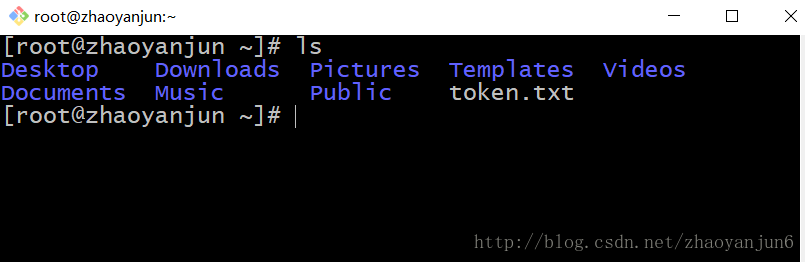
 CentOS文件权限查看和修改 文件权限查看查看目录的文件,输入命令:ls查看 token.txt 文件的权限,输入命令:ls -l token.txt那么就会出现相类似的信息-rw-r--r-- 1 root root 48 Jan 8 20:14 token.txt最开始的10位数 -rw-rw-r-- 最前面那个 - 代表的是类型第一个 rw- 代表的是所有者(user)第二个 rw- 代表的是组群(group)第三个 r-- 代表的是其他人(other) 其中: r 表示文件可以被读(read) w 表示文件可以被写(write) x 表示文件可以被执行(如果它是程序的话) - 表示相应的权限还没有被授予通过上面的解释,就可以看出 token.txt 文件的权限是:当前用户本身:可读可写,没有可执行权限当前用户组群:可读不可写,没有可执行权限其他用户:可读不可写,没有可执行权限rwx 也可以用数字来代替r ------------4 w ------------2 x ------------1 - ------------0所以我们总结出权限对应的数字-rw------- (600) 只有所有者才有读和写的权限 -rw-r--r-- (644) 只有所有者才有读和写的权限,组群和其他人只有读的权限 -rwx------ (700) 只有所有者才有读,写,执行的权限 -rwxr-xr-x (755) 只有所有者才有读,写,执行的权限,组群和其他人只有读和执行的权限 -rwx--x--x (711) 只有所有者才有读,写,执行的权限,组群和其他人只有执行的权限 -rw-rw-rw- (666) 每个人都有读写的权限 -rwxrwxrwx (777) 每个人都有读写和执行的权限修改文件权限现在我们把 token.txt 文件修改为 所有用户可读可写可执行 , 也就是对应编号为 777chmod 777 token.txt效果如下:转至:http://blog.csdn.net/zhaoyanjun6/article/details/79067442
CentOS文件权限查看和修改 文件权限查看查看目录的文件,输入命令:ls查看 token.txt 文件的权限,输入命令:ls -l token.txt那么就会出现相类似的信息-rw-r--r-- 1 root root 48 Jan 8 20:14 token.txt最开始的10位数 -rw-rw-r-- 最前面那个 - 代表的是类型第一个 rw- 代表的是所有者(user)第二个 rw- 代表的是组群(group)第三个 r-- 代表的是其他人(other) 其中: r 表示文件可以被读(read) w 表示文件可以被写(write) x 表示文件可以被执行(如果它是程序的话) - 表示相应的权限还没有被授予通过上面的解释,就可以看出 token.txt 文件的权限是:当前用户本身:可读可写,没有可执行权限当前用户组群:可读不可写,没有可执行权限其他用户:可读不可写,没有可执行权限rwx 也可以用数字来代替r ------------4 w ------------2 x ------------1 - ------------0所以我们总结出权限对应的数字-rw------- (600) 只有所有者才有读和写的权限 -rw-r--r-- (644) 只有所有者才有读和写的权限,组群和其他人只有读的权限 -rwx------ (700) 只有所有者才有读,写,执行的权限 -rwxr-xr-x (755) 只有所有者才有读,写,执行的权限,组群和其他人只有读和执行的权限 -rwx--x--x (711) 只有所有者才有读,写,执行的权限,组群和其他人只有执行的权限 -rw-rw-rw- (666) 每个人都有读写的权限 -rwxrwxrwx (777) 每个人都有读写和执行的权限修改文件权限现在我们把 token.txt 文件修改为 所有用户可读可写可执行 , 也就是对应编号为 777chmod 777 token.txt效果如下:转至:http://blog.csdn.net/zhaoyanjun6/article/details/79067442 -

-
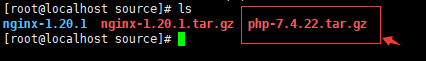
 CentOS7安装PHP 1、下载php wget https://www.php.net/distributions/php-7.4.22.tar.gz 这里下载的是7.4.22,其他版本官网下载2、解压 tar -zvxf php-7.4.22.tar.gz 3、进入目录 cd php-7.4.22 4、进行预编译 ./configure --prefix=/home/php --enable-fpm 后面编译携带参数可以使用 ./configure --help 查看具体说明 --prefix=/home/php #这里是指定安装目录 --enable-fpm #这里是PHPFastCGI管理器,为了后面Nginx能解析PHP 后面可以加一些常用的PHP扩展一起编译 , 这样安装后就自带这些扩展。出现错误 configure: error: Package requirements (libxml-2.0 >= 2.7.6) were not met: 解决方法: yum -y install libxml2-devel出现错误 configure: error: Package requirements (sqlite3 > 3.7.4) were not met: 解决方法: yum -y install sqlite-devel出现表示预编译成功5、安装 make && make install 这里需要点时间安装成功,到这里才发现我装错地方了,不过不影响使用。6、启动 复制代码cd /home/php/ #先进入安装目录 mv ./etc/php-fpm.conf.default ./etc/php-fpm.conf #重命名配置文件 mv ./etc/php-fpm.d/www.conf.default ./etc/php-fpm.d/www.conf #重命名配置文件 ./sbin/php-fpm #启动 ps -aux |grep php-fpm #查看启动状态(下面成功启动) 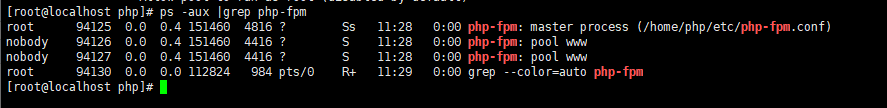 复制代码7、使用Nginx解析PHP, 编辑文章 centOS7安装、配置nginx,常用命令及禁用IP访问 进入到nginx安装目录 cd /opt/nginx/ 修改配置文件 vim ./conf/nginx.conf 修改内容如下(1)增加index.php(2)取消注释(3)修改路径保存退出 ,重启Nginx ./sbin/nginx -s reload 然后在 html 目录下面 vim index.php 写入内容保存退出,打开浏览器访问 结束安装。参考资料https://www.cnblogs.com/-wei/p/15222477.html
CentOS7安装PHP 1、下载php wget https://www.php.net/distributions/php-7.4.22.tar.gz 这里下载的是7.4.22,其他版本官网下载2、解压 tar -zvxf php-7.4.22.tar.gz 3、进入目录 cd php-7.4.22 4、进行预编译 ./configure --prefix=/home/php --enable-fpm 后面编译携带参数可以使用 ./configure --help 查看具体说明 --prefix=/home/php #这里是指定安装目录 --enable-fpm #这里是PHPFastCGI管理器,为了后面Nginx能解析PHP 后面可以加一些常用的PHP扩展一起编译 , 这样安装后就自带这些扩展。出现错误 configure: error: Package requirements (libxml-2.0 >= 2.7.6) were not met: 解决方法: yum -y install libxml2-devel出现错误 configure: error: Package requirements (sqlite3 > 3.7.4) were not met: 解决方法: yum -y install sqlite-devel出现表示预编译成功5、安装 make && make install 这里需要点时间安装成功,到这里才发现我装错地方了,不过不影响使用。6、启动 复制代码cd /home/php/ #先进入安装目录 mv ./etc/php-fpm.conf.default ./etc/php-fpm.conf #重命名配置文件 mv ./etc/php-fpm.d/www.conf.default ./etc/php-fpm.d/www.conf #重命名配置文件 ./sbin/php-fpm #启动 ps -aux |grep php-fpm #查看启动状态(下面成功启动)  复制代码7、使用Nginx解析PHP, 编辑文章 centOS7安装、配置nginx,常用命令及禁用IP访问 进入到nginx安装目录 cd /opt/nginx/ 修改配置文件 vim ./conf/nginx.conf 修改内容如下(1)增加index.php(2)取消注释(3)修改路径保存退出 ,重启Nginx ./sbin/nginx -s reload 然后在 html 目录下面 vim index.php 写入内容保存退出,打开浏览器访问 结束安装。参考资料https://www.cnblogs.com/-wei/p/15222477.html -
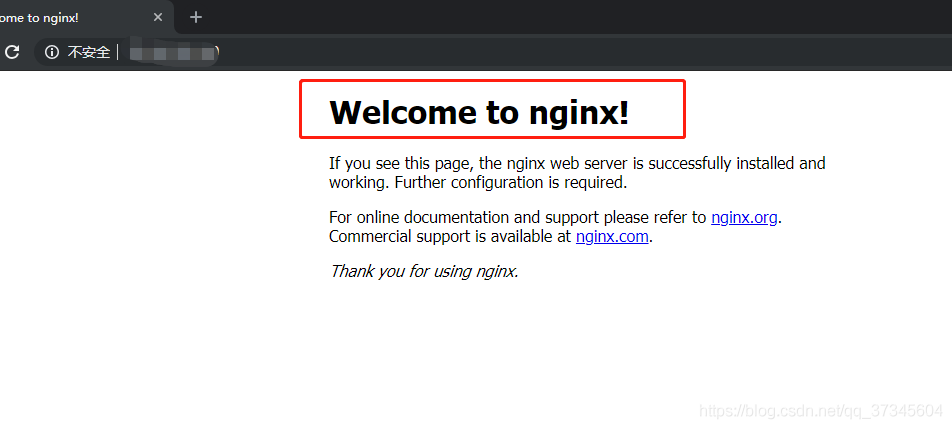
 centOS7安装、配置nginx,常用命令及禁用IP访问 安装所需插件1、安装gccgcc是linux下的编译器在此不多做解释,感兴趣的小伙伴可以去查一下相关资料,它可以编译 C,C++,Ada,Object C和Java等语言命令:查看gcc版本gcc -v一般阿里云的centOS7里面是都有的,没有安装的话会提示命令找不到,安装命令:yum -y install gcc2、pcre、pcre-devel安装pcre是一个perl库,包括perl兼容的正则表达式库,nginx的http模块使用pcre来解析正则表达式,所以需要安装pcre库。安装命令:yum install -y pcre pcre-devel3、zlib安装zlib库提供了很多种压缩和解压缩方式nginx使用zlib对http包的内容进行gzip,所以需要安装安装命令:yum install -y zlib zlib-devel4、安装opensslopenssl是web安全通信的基石,没有openssl,可以说我们的信息都是在裸奔。。。。。。安装命令:yum install -y openssl openssl-devel安装nginx1、下载nginx安装包wget http://nginx.org/download/nginx-1.9.9.tar.gz 2、把压缩包解压到usr/local/javatar -zxvf nginx-1.9.9.tar.gz3、切换到cd /usr/local/java/nginx-1.9.9/下面执行三个命令:./configure make make install4、切换到/usr/local/nginx安装目录5、配置nginx的配置文件nginx.conf文件,主要也就是端口可以按照自己服务器的端口使用情况来进行配置ESC键,wq!强制保存并退出6、启动nginx服务切换目录到/usr/local/nginx/sbin下面启动nginx命令:./nginx7、查看nginx服务是否启动成功ps -ef | grep nginx8、访问你的服务器IP显示说明安装和配置都没问题OK了nginx.conf说明#user nobody; worker_processes 1; #工作进程:数目。根据硬件调整,通常等于cpu数量或者2倍cpu数量。 #错误日志存放路径 #error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; # nginx进程pid存放路径 events { worker_connections 1024; # 工作进程的最大连接数量 } http { include mime.types; #指定mime类型,由mime.type来定义 default_type application/octet-stream; # 日志格式设置 #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; #用log_format指令设置日志格式后,需要用access_log来指定日志文件存放路径 sendfile on; #指定nginx是否调用sendfile函数来输出文件,对于普通应用,必须设置on。 如果用来进行下载等应用磁盘io重负载应用,可设着off,以平衡磁盘与网络io处理速度,降低系统uptime。 #tcp_nopush on; #此选项允许或禁止使用socket的TCP_CORK的选项,此选项仅在sendfile的时候使用 #keepalive_timeout 0; #keepalive超时时间 keepalive_timeout 65; #gzip on; #开启gzip压缩服务 #虚拟主机 server { listen 80; #配置监听端口号 server_name localhost; #配置访问域名,域名可以有多个,用空格隔开 #charset koi8-r; #字符集设置 #access_log logs/host.access.log main; location / { root html; index index.html index.htm; } #错误跳转页 #error_page 404 /404.html; # redirect server error pages to the static page /50x.html # error_page 500 502 503 504 /50x.html; location = /50x.html { root html; } # proxy the PHP scripts to Apache listening on 127.0.0.1:80 # #location ~ \.php$ { # proxy_pass http://127.0.0.1; #} # pass the PHP scripts to FastCGI server listening on 127.0.0.1:9000 # #location ~ \.php$ { #请求的url过滤,正则匹配,~为区分大小写,~*为不区分大小写。 # root html; #根目录 # fastcgi_pass 127.0.0.1:9000; #请求转向定义的服务器列表 # fastcgi_index index.php; # 如果请求的Fastcgi_index URI是以 / 结束的, 该指令设置的文件会被附加到URI的后面并保存在变量$fastcig_script_name中 # fastcgi_param SCRIPT_FILENAME /scripts$fastcgi_script_name; # include fastcgi_params; #} # deny access to .htaccess files, if Apache's document root # concurs with nginx's one # #location ~ /\.ht { # deny all; #} } # another virtual host using mix of IP-, name-, and port-based configuration # #server { # listen 8000; # listen somename:8080; # server_name somename alias another.alias; # location / { # root html; # index index.html index.htm; # } #} # HTTPS server # #server { # listen 443 ssl; #监听端口 # server_name localhost; #域名 # ssl_certificate cert.pem; #证书位置 # ssl_certificate_key cert.key; #私钥位置 # ssl_session_cache shared:SSL:1m; # ssl_session_timeout 5m; # ssl_ciphers HIGH:!aNULL:!MD5; #密码加密方式 # ssl_prefer_server_ciphers on; # ssl_prefer_server_ciphers on; # # location / { # root html; # index index.html index.htm; # } #} }重启1、验证nginx配置文件是否正确方法一:进入nginx安装目录sbin下,输入命令./nginx -t看到如下显示 `nginx.conf syntax is oknginx.conf test is successful` 说明配置文件正确!方法二:在启动命令-c前加-t2、重启Nginx服务方法一:进入nginx可执行目录sbin下,输入命令./nginx -s reload 即可方法二:查找当前nginx进程号,然后输入命令:kill -HUP 进程号 实现重启nginx服务nginx只允许域名访问,禁止ip访问这里介绍修改配置文件nginx.conf两种方法:1)在server段里插入如下正则:listen 80; server_name www.yuyangblog.net; if ($host != 'www.yuyangblog.net'){ return 403; }2)添加一个server新加的server(注意是新增,并不是在原有的server基础上修改)server { listen 80 default; server_name _; return 403; }参考资料:https://blog.csdn.net/qq_37345604/article/details/90034424https://www.cnblogs.com/codingcloud/p/5095066.htmlhttps://www.cnblogs.com/weifeng1463/p/9197971.html
centOS7安装、配置nginx,常用命令及禁用IP访问 安装所需插件1、安装gccgcc是linux下的编译器在此不多做解释,感兴趣的小伙伴可以去查一下相关资料,它可以编译 C,C++,Ada,Object C和Java等语言命令:查看gcc版本gcc -v一般阿里云的centOS7里面是都有的,没有安装的话会提示命令找不到,安装命令:yum -y install gcc2、pcre、pcre-devel安装pcre是一个perl库,包括perl兼容的正则表达式库,nginx的http模块使用pcre来解析正则表达式,所以需要安装pcre库。安装命令:yum install -y pcre pcre-devel3、zlib安装zlib库提供了很多种压缩和解压缩方式nginx使用zlib对http包的内容进行gzip,所以需要安装安装命令:yum install -y zlib zlib-devel4、安装opensslopenssl是web安全通信的基石,没有openssl,可以说我们的信息都是在裸奔。。。。。。安装命令:yum install -y openssl openssl-devel安装nginx1、下载nginx安装包wget http://nginx.org/download/nginx-1.9.9.tar.gz 2、把压缩包解压到usr/local/javatar -zxvf nginx-1.9.9.tar.gz3、切换到cd /usr/local/java/nginx-1.9.9/下面执行三个命令:./configure make make install4、切换到/usr/local/nginx安装目录5、配置nginx的配置文件nginx.conf文件,主要也就是端口可以按照自己服务器的端口使用情况来进行配置ESC键,wq!强制保存并退出6、启动nginx服务切换目录到/usr/local/nginx/sbin下面启动nginx命令:./nginx7、查看nginx服务是否启动成功ps -ef | grep nginx8、访问你的服务器IP显示说明安装和配置都没问题OK了nginx.conf说明#user nobody; worker_processes 1; #工作进程:数目。根据硬件调整,通常等于cpu数量或者2倍cpu数量。 #错误日志存放路径 #error_log logs/error.log; #error_log logs/error.log notice; #error_log logs/error.log info; #pid logs/nginx.pid; # nginx进程pid存放路径 events { worker_connections 1024; # 工作进程的最大连接数量 } http { include mime.types; #指定mime类型,由mime.type来定义 default_type application/octet-stream; # 日志格式设置 #log_format main '$remote_addr - $remote_user [$time_local] "$request" ' # '$status $body_bytes_sent "$http_referer" ' # '"$http_user_agent" "$http_x_forwarded_for"'; #access_log logs/access.log main; #用log_format指令设置日志格式后,需要用access_log来指定日志文件存放路径 sendfile on; #指定nginx是否调用sendfile函数来输出文件,对于普通应用,必须设置on。 如果用来进行下载等应用磁盘io重负载应用,可设着off,以平衡磁盘与网络io处理速度,降低系统uptime。 #tcp_nopush on; #此选项允许或禁止使用socket的TCP_CORK的选项,此选项仅在sendfile的时候使用 #keepalive_timeout 0; #keepalive超时时间 keepalive_timeout 65; #gzip on; #开启gzip压缩服务 #虚拟主机 server { listen 80; #配置监听端口号 server_name localhost; #配置访问域名,域名可以有多个,用空格隔开 #charset koi8-r; #字符集设置 #access_log logs/host.access.log main; location / { root html; index index.html index.htm; } #错误跳转页 #error_page 404 /404.html; # redirect server error pages to the static page /50x.html # error_page 500 502 503 504 /50x.html; location = /50x.html { root html; } # proxy the PHP scripts to Apache listening on 127.0.0.1:80 # #location ~ \.php$ { # proxy_pass http://127.0.0.1; #} # pass the PHP scripts to FastCGI server listening on 127.0.0.1:9000 # #location ~ \.php$ { #请求的url过滤,正则匹配,~为区分大小写,~*为不区分大小写。 # root html; #根目录 # fastcgi_pass 127.0.0.1:9000; #请求转向定义的服务器列表 # fastcgi_index index.php; # 如果请求的Fastcgi_index URI是以 / 结束的, 该指令设置的文件会被附加到URI的后面并保存在变量$fastcig_script_name中 # fastcgi_param SCRIPT_FILENAME /scripts$fastcgi_script_name; # include fastcgi_params; #} # deny access to .htaccess files, if Apache's document root # concurs with nginx's one # #location ~ /\.ht { # deny all; #} } # another virtual host using mix of IP-, name-, and port-based configuration # #server { # listen 8000; # listen somename:8080; # server_name somename alias another.alias; # location / { # root html; # index index.html index.htm; # } #} # HTTPS server # #server { # listen 443 ssl; #监听端口 # server_name localhost; #域名 # ssl_certificate cert.pem; #证书位置 # ssl_certificate_key cert.key; #私钥位置 # ssl_session_cache shared:SSL:1m; # ssl_session_timeout 5m; # ssl_ciphers HIGH:!aNULL:!MD5; #密码加密方式 # ssl_prefer_server_ciphers on; # ssl_prefer_server_ciphers on; # # location / { # root html; # index index.html index.htm; # } #} }重启1、验证nginx配置文件是否正确方法一:进入nginx安装目录sbin下,输入命令./nginx -t看到如下显示 `nginx.conf syntax is oknginx.conf test is successful` 说明配置文件正确!方法二:在启动命令-c前加-t2、重启Nginx服务方法一:进入nginx可执行目录sbin下,输入命令./nginx -s reload 即可方法二:查找当前nginx进程号,然后输入命令:kill -HUP 进程号 实现重启nginx服务nginx只允许域名访问,禁止ip访问这里介绍修改配置文件nginx.conf两种方法:1)在server段里插入如下正则:listen 80; server_name www.yuyangblog.net; if ($host != 'www.yuyangblog.net'){ return 403; }2)添加一个server新加的server(注意是新增,并不是在原有的server基础上修改)server { listen 80 default; server_name _; return 403; }参考资料:https://blog.csdn.net/qq_37345604/article/details/90034424https://www.cnblogs.com/codingcloud/p/5095066.htmlhttps://www.cnblogs.com/weifeng1463/p/9197971.html